Quiz Summary
0 of 51 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 51 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- Current
- Review / Skip
- Answered
- Correct
- Incorrect
-
Question 1 of 51
1. Question
The integrity of data is not related to which of the following?
CorrectIncorrect -
Question 2 of 51
2. Question
Which of the following steps comes first in a business impact analysis?
CorrectIncorrect -
Question 3 of 51
3. Question
Which of the following was the first international treaty seeking to address computer crimes by coordinating national laws and improving investigative techniques and international cooperation?
CorrectIncorrect -
Question 4 of 51
4. Question
As his company’s CISO, George needs to demonstrate to the board of directors the necessity of a strong risk management program. Which of the following should George use to calculate the company’s residual risk?
CorrectIncorrect -
Question 5 of 51
5. Question
It is not unusual for business continuity plans to become out of date. Which of the following is not a reason why plans become outdated?
CorrectIncorrect -
Question 6 of 51
6. Question
Lee is a new security manager who is in charge of ensuring that his company complies with the European Union Principles on Privacy when his company is interacting with their European partners. The set of principles that deals with transmitting data considered private is encompassed within which of the following laws or regulations?
CorrectIncorrect -
Question 7 of 51
7. Question
Capability Maturity Model Integration (CMMI) came from the software engineering world and is used within organizations to help lay out a pathway of how incremental improvement can take place. This model is used by organizations in self-assessment and to develop structured steps that can be followed so an organization can evolve from one level to the next and constantly improve its processes. In the CMMI model graphic shown, what is the proper sequence of the levels?
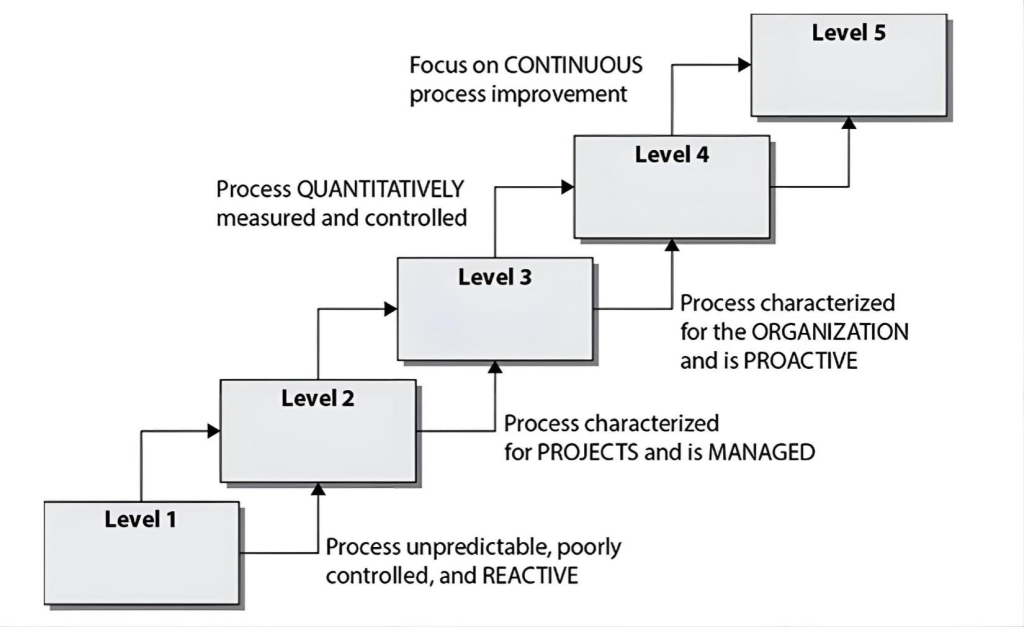 CorrectIncorrect
CorrectIncorrect -
Question 8 of 51
8. Question
Preplanned business continuity procedures provide organizations a number of benefits. Which of the following is not a capability enabled by business continuity planning?
CorrectIncorrect -
Question 9 of 51
9. Question
Brandy could not figure out how Sam gained unauthorized access to her system, since he has little computer experience. Which of the following is most likely the attack Sam used?
CorrectIncorrect -
Question 10 of 51
10. Question
Risk assessment has several different methodologies. Which of the following official risk methodologies was not created for the purpose of analyzing security risks?
CorrectIncorrect -
Question 11 of 51
11. Question
Management support is critical to the success of a business continuity plan. Which of the following is the most important to be provided to management to obtain their support?
CorrectIncorrect -
Question 12 of 51
12. Question
Jane has been charged with ensuring that the privacy of clients’ personal health information is adequately protected before it is exchanged with a new European partner. What data security requirements must she adhere to?
CorrectIncorrect -
Question 13 of 51
13. Question
Which of the following is not a characteristic of a company with a security governance program in place?
CorrectIncorrect -
Question 14 of 51
14. Question
Which of the following is a critical first step in disaster recovery and contingency planning?
CorrectIncorrect -
Question 15 of 51
15. Question
Sue has been tasked with implementing a number of security controls, including antivirus and antispam software, to protect the company’s e-mail system. What type of approach is her company taking to handle the risk posed by the system?
CorrectIncorrect -
Question 16 of 51
16. Question
There are four ways of dealing with risk. In the graphic that follows, which method is missing and what is the purpose of this method?
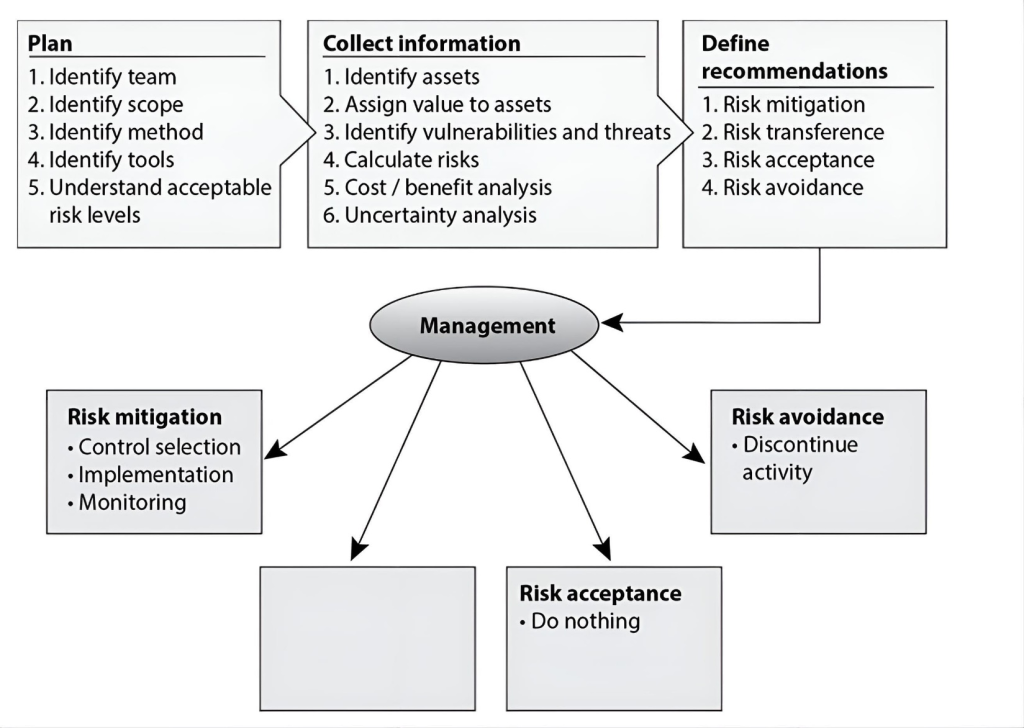 CorrectIncorrect
CorrectIncorrect -
Question 17 of 51
17. Question
Which of the following is not a reason to develop and implement a disaster recovery plan?
CorrectIncorrect -
Question 18 of 51
18. Question
A number of factors should be considered when assigning values to assets. Which of the following is not used to determine the value of an asset?
CorrectIncorrect -
Question 19 of 51
19. Question
The following graphic contains a commonly used risk management scorecard. Identify the proper quadrant and its description.
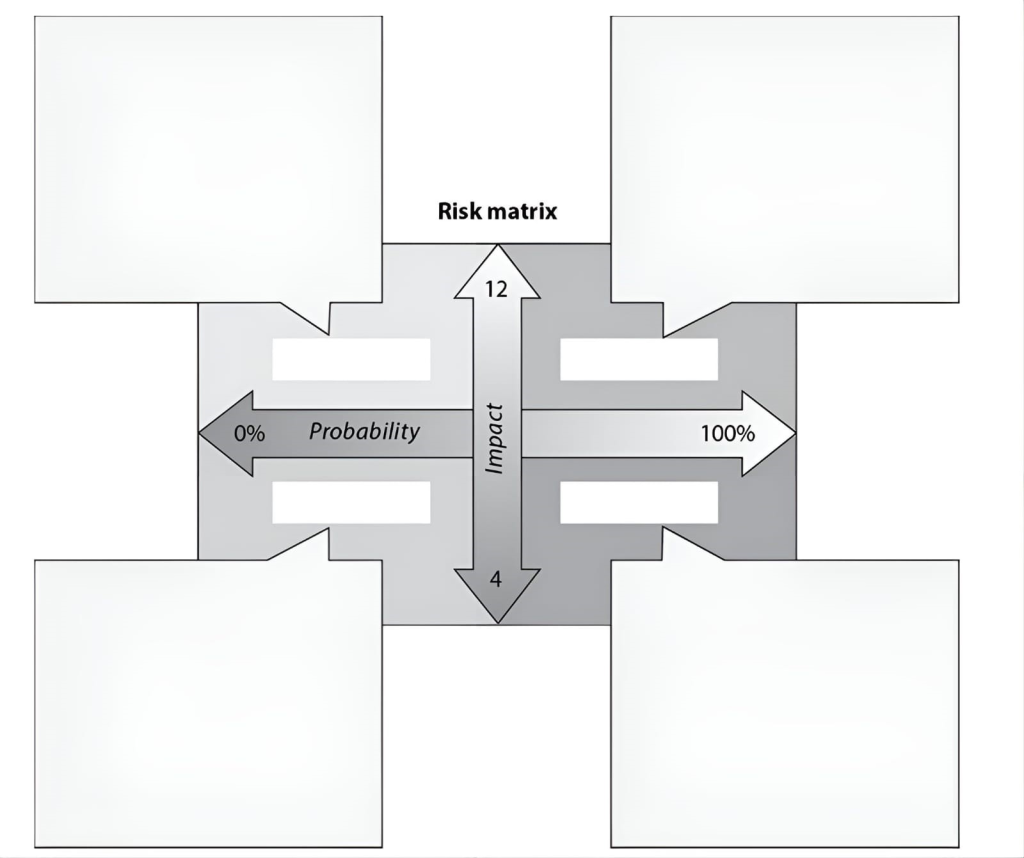 CorrectIncorrect
CorrectIncorrect -
Question 20 of 51
20. Question
With what phase of a business continuity plan does a company proceed when it is ready to move back into its original site or a new site?
CorrectIncorrect -
Question 21 of 51
21. Question
The Zachman Architecture Framework is often used to set up an enterprise security architecture. Which of the following does not correctly describe the Zachman Framework?
CorrectIncorrect -
Question 22 of 51
22. Question
What are the three types of policies that are missing from the following graphic?
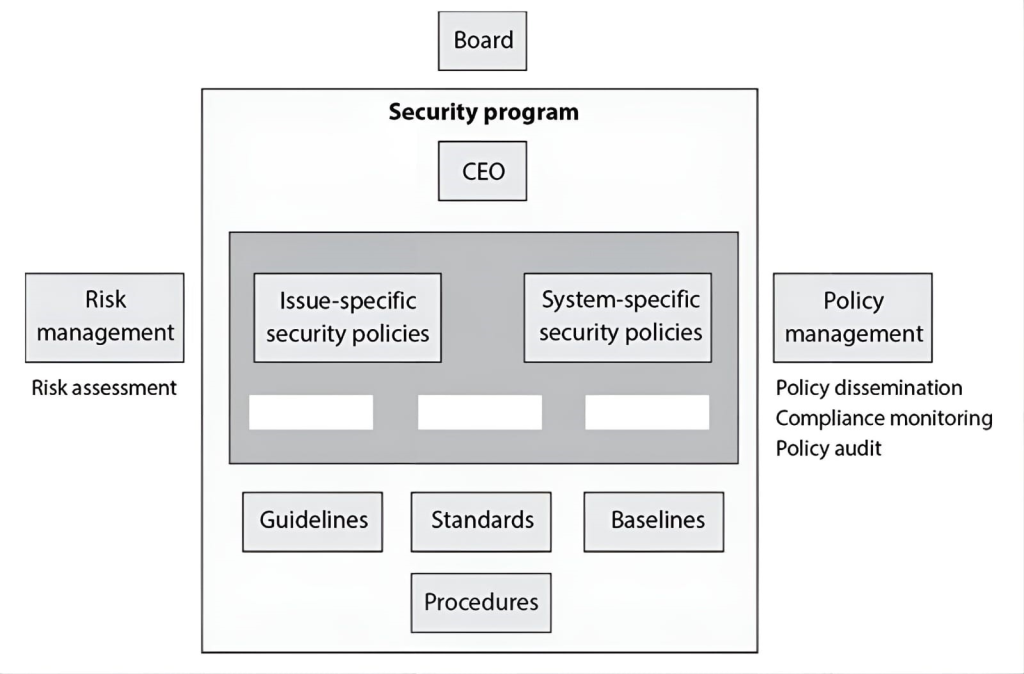 CorrectIncorrect
CorrectIncorrect -
Question 23 of 51
23. Question
What is the missing second step in the graphic that follows?
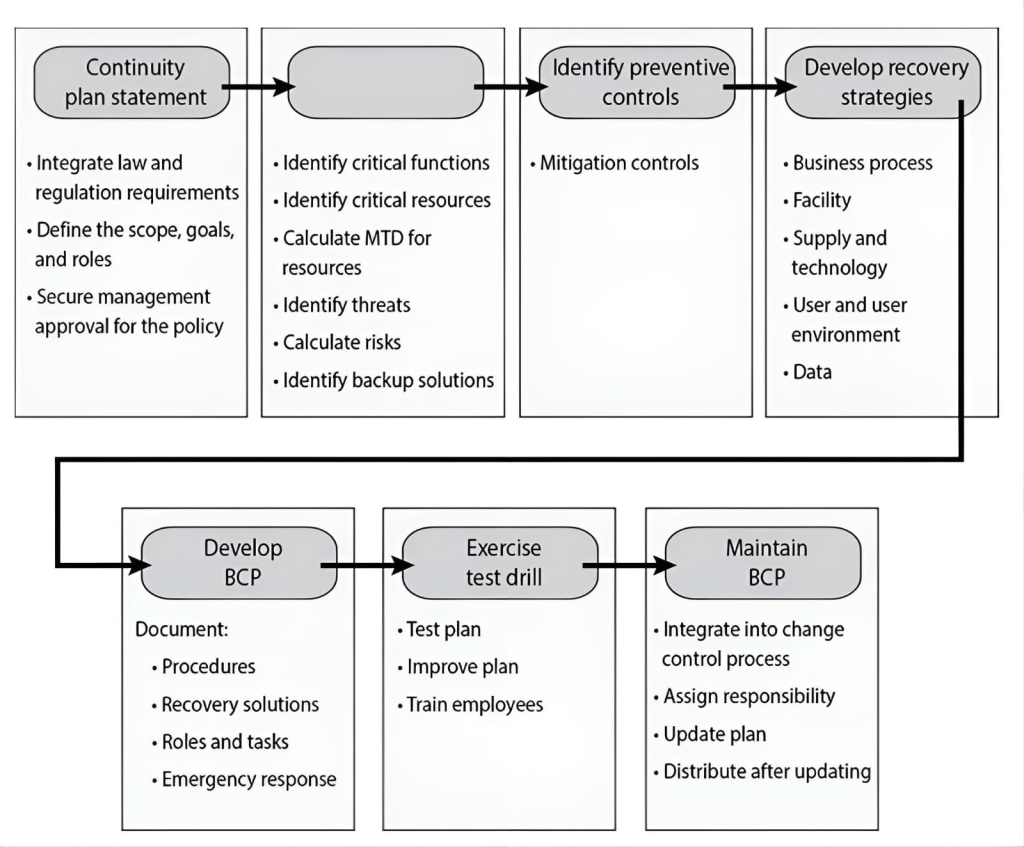 CorrectIncorrect
CorrectIncorrect -
Question 24 of 51
24. Question
John has been told to report to the board of directors with a vendor-neutral enterprise architecture framework that will help the company reduce fragmentation that results from the misalignment of IT and business processes. Which of the following frameworks should he suggest?
CorrectIncorrect -
Question 25 of 51
25. Question
List in the proper order from the table shown the learning objectives that are missing and their proper definitions.
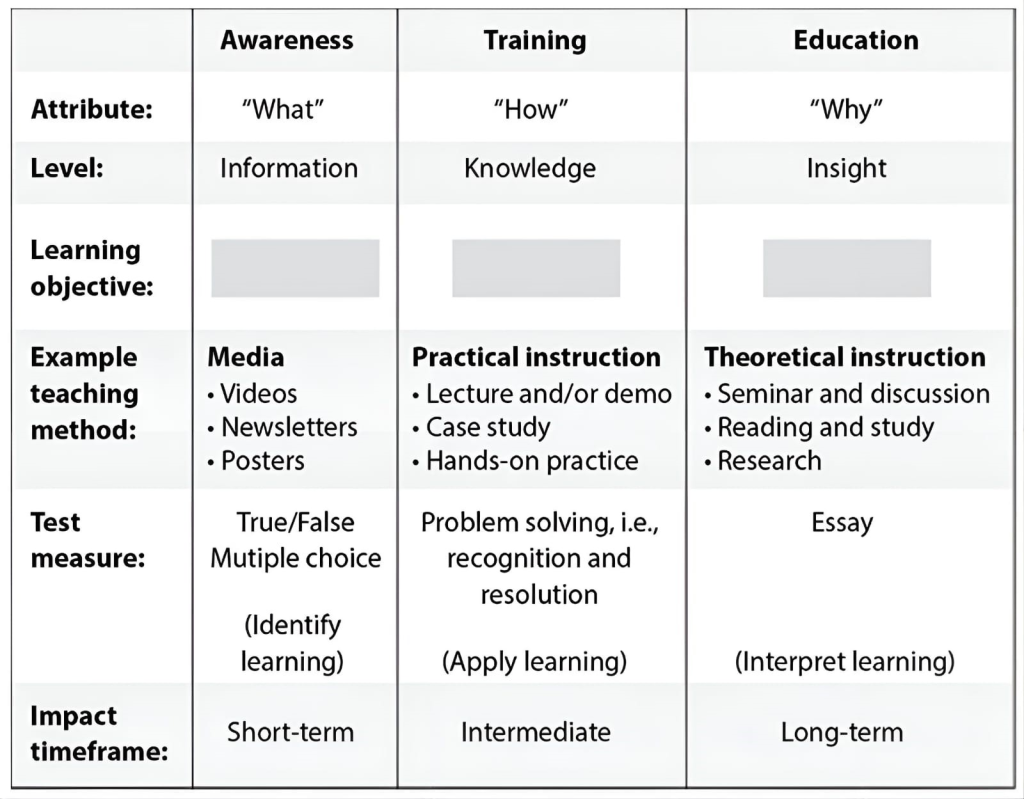 CorrectIncorrect
CorrectIncorrect -
Question 26 of 51
26. Question
Different threats need to be evaluated and ranked based upon their severity of business risk when developing a BCP. Which ranking approach is illustrated in the graphic that follows?
 CorrectIncorrect
CorrectIncorrect -
Question 27 of 51
27. Question
The Information Technology Infrastructure Library (ITIL) consists of five sets of instructional books. Which of the following is considered the core set and focuses on the overall planning of the intended IT services?
CorrectIncorrect -
Question 28 of 51
28. Question
What type of risk analysis approach does the following graphic provide?
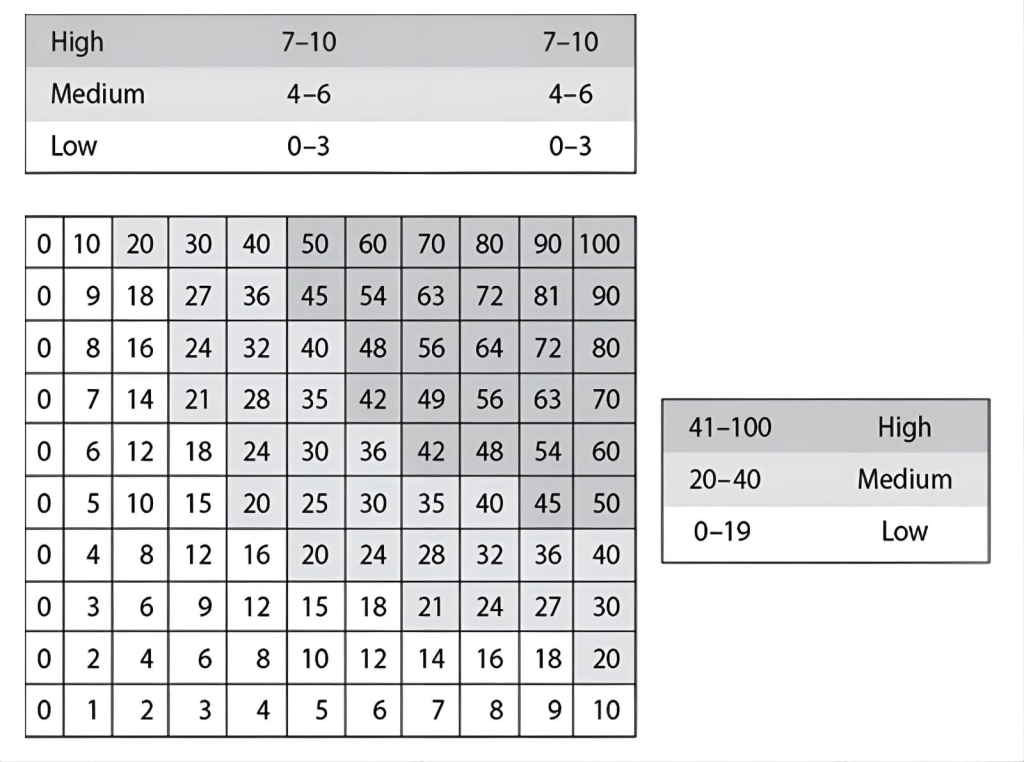 CorrectIncorrect
CorrectIncorrect -
Question 29 of 51
29. Question
Sean has been hired as business continuity coordinator. He has been told by management that he needs to ensure that the company is in compliance with the ISO/IEC standard that pertains to technology readiness for business continuity. He has also been instructed to find a way to transfer the risk of being unable to carry out critical business functions for a period of time because of a disaster. Which of the following is most likely the standard that Sean has been asked to comply with?
CorrectIncorrect -
Question 30 of 51
30. Question
Sarah and her security team have carried out many vulnerability tests over the years to locate the weaknesses and vulnerabilities within the systems on the network. The CISO has asked her to oversee the development of a threat model for the network. Which of the following best describes what this model is and what it would be used for?
CorrectIncorrect -
Question 31 of 51
31. Question
ISO/IEC 27000 is part of a growing family of ISO/IEC information security management systems (ISMS) standards. It comprises information security standards published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). Which of the following provides an incorrect mapping of the individual standards that make up this family of standards ?
CorrectIncorrect -
Question 32 of 51
32. Question
Which organization has been developed to deal with economic, social, and governance issues and with how sensitive data is transported over borders?
CorrectIncorrect -
Question 33 of 51
33. Question
Health Tracking Apps, Inc. (HTA) is a U.S.-based corporation that develops and sells apps that its customers can use to track various aspects of their own health, from their daily exercise regimes to various medical test results and comparative statistics over time. These apps utilize cloud-based storage so that customers can access their data from multiple platforms, including smart mobile devices and desktop systems. Customers can also easily share the data the apps generate with their personal trainers and healthcare providers if they choose, on a subscription basis.
HTA’s products are available in several languages, including English, French, Spanish, German, and Italian. All of HTA’s software is developed by a dedicated staff within the United States, though HTA occasionally hires interns from the local university to assist with language translations for its various user interfaces.
The following entity relationship diagram illustrates HTA’s business model dependencies: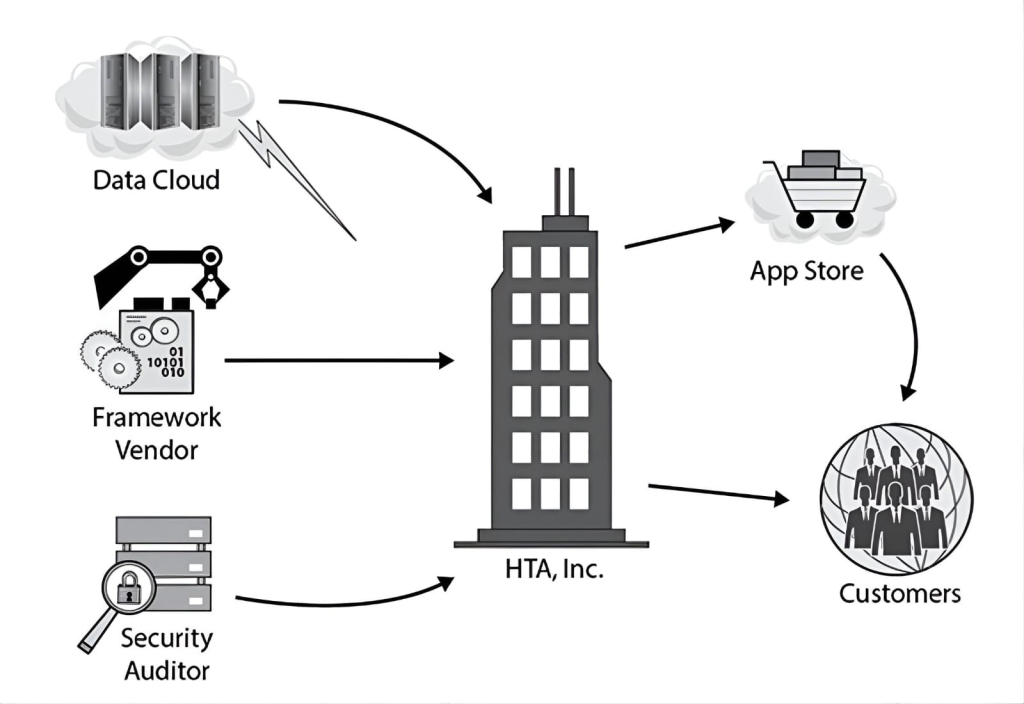
Would HTA be required to comply with the General Data Protection Regulation (GDPR)? If so, why? If not, why?
1. Maybe, because HTA’s HR records could contain protected privacy data about European citizens if any of HTA’s interns are students studying from abroad.
2. No, because the GDPR applies only to European-based companies.
3. Yes, to the extent that HTA’s stored private data includes that of any European customers.
4. No, because any private data regarding European citizens that HTA’s HR and customer records contain is stored within the United States.CorrectIncorrect -
Question 34 of 51
34. Question
Which of the following is the criteria Sam’s company was most likely certified under?
CorrectIncorrect -
Question 35 of 51
35. Question
Widgets, Inc., wishes to protect its logo from unauthorized use. Which of the following will protect the logo and ensure that others cannot copy and use it?
CorrectIncorrect -
Question 36 of 51
36. Question
Health Tracking Apps, Inc. (HTA) is a U.S.-based corporation that develops and sells apps that its customers can use to track various aspects of their own health, from their daily exercise regimes to various medical test results and comparative statistics over time. These apps utilize cloud-based storage so that customers can access their data from multiple platforms, including smart mobile devices and desktop systems. Customers can also easily share the data the apps generate with their personal trainers and healthcare providers if they choose, on a subscription basis.
HTA’s products are available in several languages, including English, French, Spanish, German, and Italian. All of HTA’s software is developed by a dedicated staff within the United States, though HTA occasionally hires interns from the local university to assist with language translations for its various user interfaces.
The following entity relationship diagram illustrates HTA’s business model dependencies: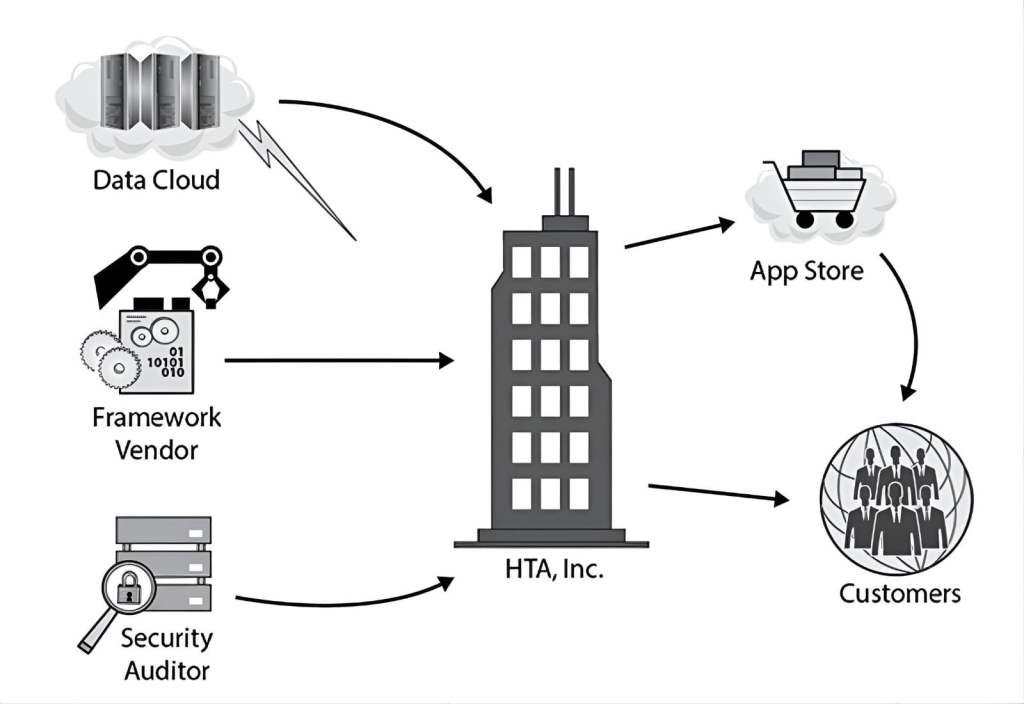
HTA’s customer data is breached via a vulnerability in its application programming interface (API). This vulnerability is discovered to be a result of a recently announced security flaw in the underlying Java framework that HTA uses for the development of its apps. Which of the following best describes the root of this problem?
CorrectIncorrect -
Question 37 of 51
37. Question
Which of the following best describes the relationship between COBIT and ITIL?
CorrectIncorrect -
Question 38 of 51
38. Question
What is the associated single loss expectancy value in this scenario?
CorrectIncorrect -
Question 39 of 51
39. Question
Which of the following means that a company did all it could have reasonably done to prevent a security breach?
CorrectIncorrect -
Question 40 of 51
40. Question
Health Tracking Apps, Inc. (HTA) is a U.S.-based corporation that develops and sells apps that its customers can use to track various aspects of their own health, from their daily exercise regimes to various medical test results and comparative statistics over time. These apps utilize cloud-based storage so that customers can access their data from multiple platforms, including smart mobile devices and desktop systems. Customers can also easily share the data the apps generate with their personal trainers and healthcare providers if they choose, on a subscription basis.
HTA’s products are available in several languages, including English, French, Spanish, German, and Italian. All of HTA’s software is developed by a dedicated staff within the United States, though HTA occasionally hires interns from the local university to assist with language translations for its various user interfaces.
The following entity relationship diagram illustrates HTA’s business model dependencies: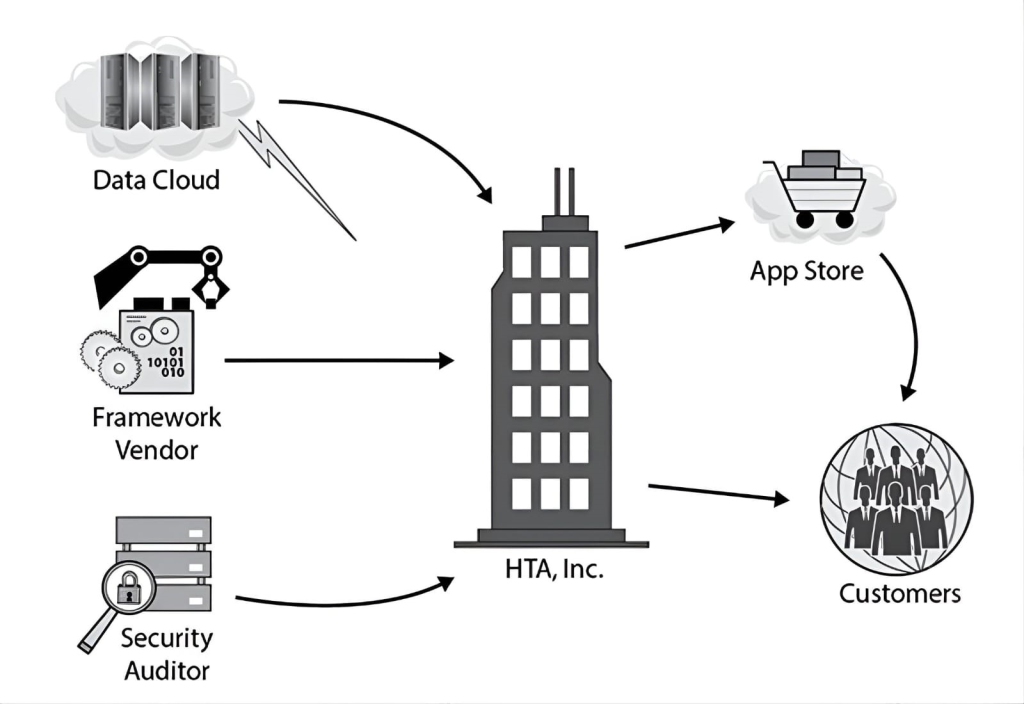
HTA stores its customers’ private data in a third-party cloud. What is the primary means through which HTA can ensure that its cloud service provider maintains compliance with any regulations—including the GDPR, if necessary—that HTA is subject to?
CorrectIncorrect -
Question 41 of 51
41. Question
Global organizations that transfer data across international boundaries must abide by guidelines and transborder information flow rules developed by an international organization that helps different governments come together and tackle the economic, social, and governance challenges of a globalized economy. What organization is this?
CorrectIncorrect -
Question 42 of 51
42. Question
The NIST organization has defined best practices for creating continuity plans. Which of the following phases deals with identifying and prioritizing critical functions and systems?
CorrectIncorrect -
Question 43 of 51
43. Question
Which of the following is a U.S. copyright law that criminalizes the production and dissemination of technology, devices, or services that circumvent access control measures put into place to protect copyright material?
CorrectIncorrect -
Question 44 of 51
44. Question
Health Tracking Apps, Inc. (HTA) is a U.S.-based corporation that develops and sells apps that its customers can use to track various aspects of their own health, from their daily exercise regimes to various medical test results and comparative statistics over time. These apps utilize cloud-based storage so that customers can access their data from multiple platforms, including smart mobile devices and desktop systems. Customers can also easily share the data the apps generate with their personal trainers and healthcare providers if they choose, on a subscription basis.
HTA’s products are available in several languages, including English, French, Spanish, German, and Italian. All of HTA’s software is developed by a dedicated staff within the United States, though HTA occasionally hires interns from the local university to assist with language translations for its various user interfaces.
The following entity relationship diagram illustrates HTA’s business model dependencies: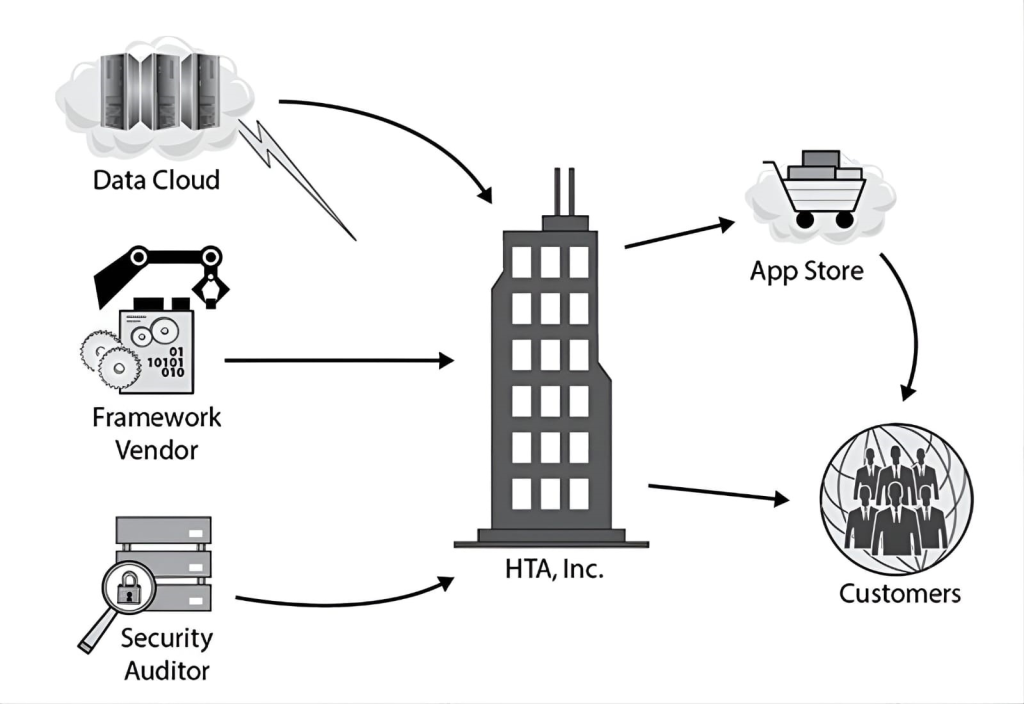
Many of HTA’s employees have either direct or indirect access to its customers’ private data. HTA has to ensure that newly hired employees are aware of all security policies and procedures that apply to them, have only the necessary access through the accounts created for them, and have signed an agreement not to disclose the data inappropriately. Which of the following terms describes this process?
CorrectIncorrect -
Question 45 of 51
45. Question
Steve, a department manager, has been asked to join a committee that is responsible for defining an acceptable level of risk for the organization, reviewing risk assessment and audit reports, and approving significant changes to security policies and programs. What committee is he joining?
CorrectIncorrect -
Question 46 of 51
46. Question
As his company’s business continuity coordinator, Matthew is responsible for helping recruit members to the business continuity planning (BCP) committee. Which of the following does not correctly describe this effort?
CorrectIncorrect -
Question 47 of 51
47. Question
What role does the Internet Architecture Board play regarding technology and ethics?
CorrectIncorrect -
Question 48 of 51
48. Question
Health Tracking Apps, Inc. (HTA) is a U.S.-based corporation that develops and sells apps that its customers can use to track various aspects of their own health, from their daily exercise regimes to various medical test results and comparative statistics over time. These apps utilize cloud-based storage so that customers can access their data from multiple platforms, including smart mobile devices and desktop systems. Customers can also easily share the data the apps generate with their personal trainers and healthcare providers if they choose, on a subscription basis.
HTA’s products are available in several languages, including English, French, Spanish, German, and Italian. All of HTA’s software is developed by a dedicated staff within the United States, though HTA occasionally hires interns from the local university to assist with language translations for its various user interfaces.
The following entity relationship diagram illustrates HTA’s business model dependencies: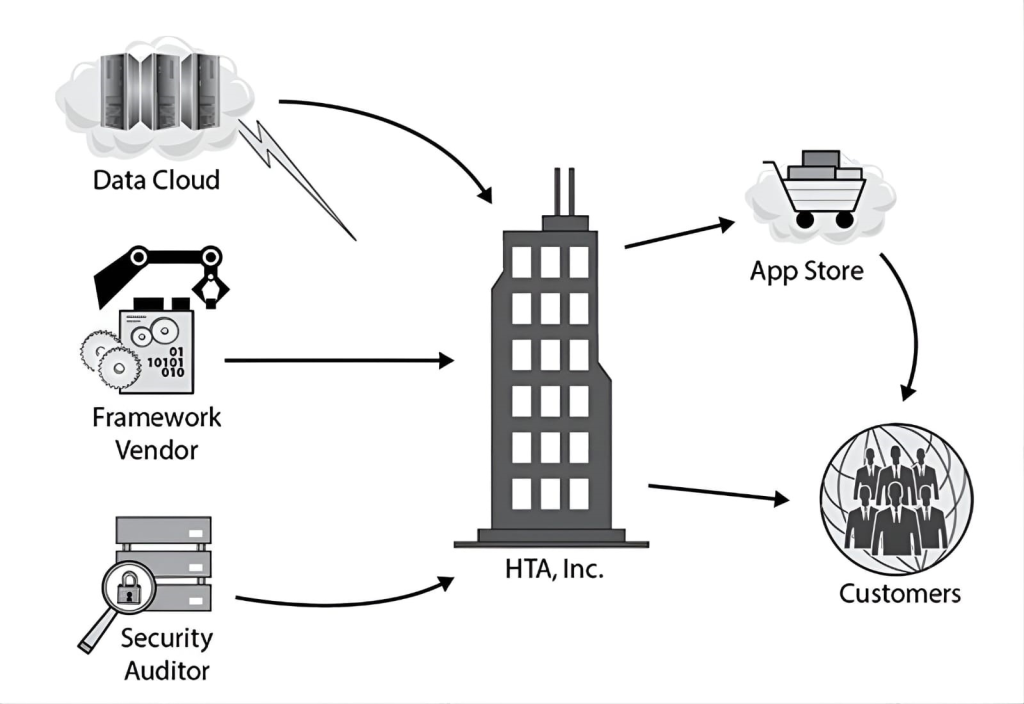
HTA has an awareness program designed to educate all employees about security-relevant issues that apply to them, based on their role. IT staff members are specifically instructed that it is important to be aware of new vulnerabilities as they are discovered, not only in the OSs that are used by HTA, but also in the applications and frameworks the developers use to build their software. The awareness program also stresses the importance of rapid mitigation by IT staff. As stated in question 48, HTA’s customer data has been breached via a vulnerability in its API, a vulnerability discovered to be a result of a recently announced security flaw in the underlying Java framework that HTA uses for the development of its apps. Which of the following most likely contributed to the breach with respect to the security awareness program?
CorrectIncorrect -
Question 49 of 51
49. Question
Which of the following is not included in a risk assessment?
CorrectIncorrect -
Question 50 of 51
50. Question
A business impact analysis is considered a functional analysis. Which of the following is not carried out during a business impact analysis?
CorrectIncorrect -
Question 51 of 51
51. Question
As a CISSP candidate, you must sign a Code of Ethics. Which of the following is from the (ISC)² Code of Ethics for the CISSP?
CorrectIncorrect